Updated February 2025: Stop getting error messages and slow down your system with our optimization tool. Get it now at this link
- Download and install the repair tool here.
- Let it scan your computer.
- The tool will then repair your computer.
Computer encryption is based on the science of cryptography, which has been used since people wanted to keep information secret. Most forms of cryptography used today are computer-based, simply because a human-based code is too easy for a computer to decipher. Cryptosystems use a number of techniques known as cryptographic or encryption algorithms to encrypt plain text messages into encrypted or ciphered messages or to decrypt plain text messages.

Algorithms
An algorithm is essentially a method or formula for solving a data mining problem. An encryption algorithm is a set of mathematical procedures for performing data encryption. Using such an algorithm, information is made in ciphertext and requires the use of a key to convert the data into its original form. This brings us to the concept of cryptography, which has long been used for information security in communication systems.
Cryptography
Cryptography is a method of applying advanced mathematical principles to the storage and transmission of data in a specific form so that only those for whom it is intended can read and process it. Encryption is a key concept in cryptography – it is a process by which a message is encrypted in a format that cannot be read or understood by a person listening at a door. The technique is ancient and was first used by Caesar to encrypt his messages with the Caesar code. A plain text message from a user can be encrypted into ciphertext and then sent over a communication channel, without any earphones interfering with the plain text. When it reaches the recipient, the ciphertext is decrypted to become the original plain text.
February 2025 Update:
You can now prevent PC problems by using this tool, such as protecting you against file loss and malware. Additionally, it is a great way to optimize your computer for maximum performance. The program fixes common errors that might occur on Windows systems with ease - no need for hours of troubleshooting when you have the perfect solution at your fingertips:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
Symmetric Encryption
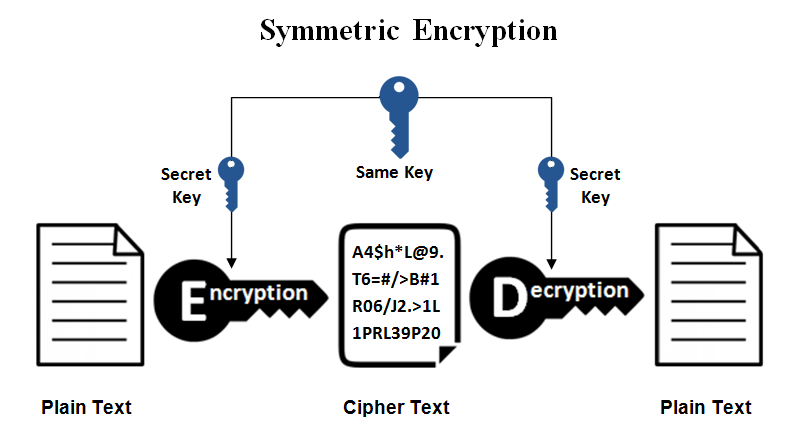
Symmetric encryption is a classic encryption method. It is also the simpler of the two techniques. Symmetric encryption uses only one secret key, called the “symmetric key”, which is owned by both parties. This key is used to encrypt and decrypt information. The sender uses this key before sending the message, and the recipient uses it to decrypt the encrypted message.
This technique is quite simple and therefore does not take much time. When transmitting large amounts of data, symmetric keys are preferred. Caesar’s cipher happens to be a good example of symmetric encryption. Modern approaches to symmetric encryption use algorithms such as RC4, AES, DES, 3DES, QUAD, Blowfish, etc.
The most common form of symmetric encryption occurs once an encrypted connection between a client and a server with an installed SSL certificate has been negotiated. Once the connection has been negotiated, two 256-bit session keys are created and exchanged so that the encrypted communication can take place.
Asymmetric Encryption
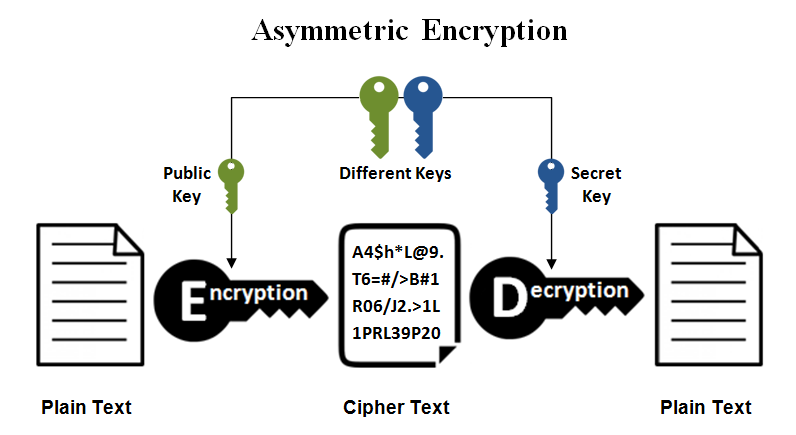
Asymmetric encryption is a relatively new and complex encryption method. Complex because it contains two cryptographic keys to implement data security. These keys are called the public key and the private key. The public key, as its name implies, is available to anyone who wishes to send a message. The private key, on the other hand, is kept in a safe place by the owner of the public key.
The public key encrypts the information to be sent. It uses a specific algorithm. The private key in the possession of the recipient decrypts it. The same algorithm is used for both procedures.
The involvement of two keys makes asymmetric encryption a complex technique. It is therefore massively advantageous in terms of data security. The Diffie-Hellman and RSA algorithms are the most widely used algorithms for asymmetric encryption.
Conclusion
Because it is a complex and slow encryption technique, asymmetric encryption is generally used for key exchange and symmetric encryption is used as a faster technique for mass data transmission.
Expert Tip: This repair tool scans the repositories and replaces corrupt or missing files if none of these methods have worked. It works well in most cases where the problem is due to system corruption. This tool will also optimize your system to maximize performance. It can be downloaded by Clicking Here
