Updated February 2025: Stop getting error messages and slow down your system with our optimization tool. Get it now at this link
- Download and install the repair tool here.
- Let it scan your computer.
- The tool will then repair your computer.
Network analysis and port analysis – the process of studying the structure and behavior of a network – are not hostile in nature, but attackers often use them to educate people before trying to hack a network.
How does malicious scanning work and how can you detect possible detection of your network? Let us start by defining the most basic terms:
- When scanning a network, all active hosts on the network are detected and assigned to their IP addresses.
- Port scanning is the process of sending packets to specific host ports and analyzing the responses to find out details about running services or potential weaknesses.
What is Port Scanning?
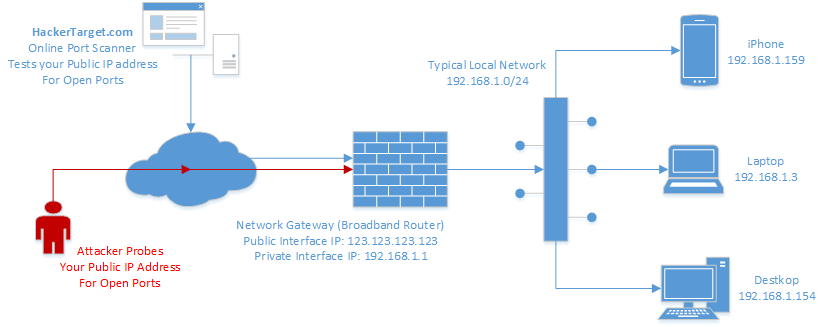
Port scanning is a method of determining which ports are open on the network and can receive or send data. It is also a process of sending packets to specific ports on the host and analyzing the responses to identify vulnerabilities. This scan cannot be done without identifying a list of active hosts and assigning those hosts their IP addresses. Once the network is thoroughly scanned and a list of hosts is compiled, it is possible to perform a corresponding port scan. By organizing IP addresses, hosts and ports, the scanner can correctly identify open or vulnerable server locations to diagnose security levels.
Ports Scanners and Ports Scanners These scans indicate that protection is available, for example. B. firewall between the server and the user’s device.
Cyber-attackers and administrators can use these scans to examine or analyze network security policies and identify vulnerabilities. and identify weak points in the cybercriminal’s case.
February 2025 Update:
You can now prevent PC problems by using this tool, such as protecting you against file loss and malware. Additionally, it is a great way to optimize your computer for maximum performance. The program fixes common errors that might occur on Windows systems with ease - no need for hours of troubleshooting when you have the perfect solution at your fingertips:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
Typically used protocols for port scanning are the Transfer Control Protocol (TCP) and the User Datagram Protocol (UDP). These are both methods of data transfer for the Internet, but they have different mechanisms. TCP is a reliable two-way transfer of data on the basis of connection which depends on a condition of a destination for termination of sending. UDP does not demand an establishment of connection and it is unreliable. The data is sent regardless of the destination. There is therefore no guarantee that the data will get there. There are several port scanning methods using these two protocols, which are described in the next section “Methods”.
Port Scanning Methods
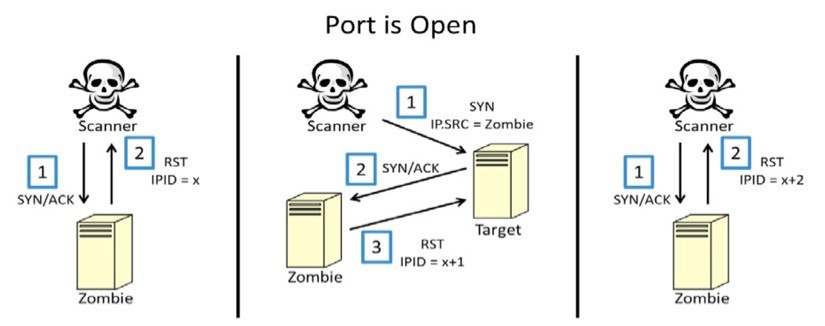
TCP and UDP are usually the protocols used in port scanning, as mentioned earlier, and there are several different methods to perform port scanning using these protocols.
The most commonly used method for TCP analysis is SYN analysis. To do this, a partial connection to a host is made on the destination port by sending a SYN packet and then evaluating the host response. If the request packet is not filtered or blocked by the firewall, the host sends a SYN / ACK packet if the port is open, or an RST packet if the port is closed.
Another method of TCP analysis is TCP connection analysis. In this case, the scanner tries to connect to a port on the destination host using the TCP Connect system call and initiates a complete TCP confirmation process. This process generates high packet overhead and it is much easier to detect, which makes it a less used port scanning method.
Other types of TCP port scans include NULL, FIN and Xmas. These three types of scans deal with TCP header flags. NULL scans send packets without flags in the header, while FIN scans only have the FIN bit set. In case of Christmas packages, the FIN, PSH and URG flag bits may glow like a Christmas tree. Hence the name “Christmas Scan”.
Like the TCP scan, the UDP scan sends a UDP packet to different ports on the destination host and evaluates the response packets to determine the service availability on the host. Like the TCP scan, receiving the response packet indicates that the port is open.
Install the port scanner
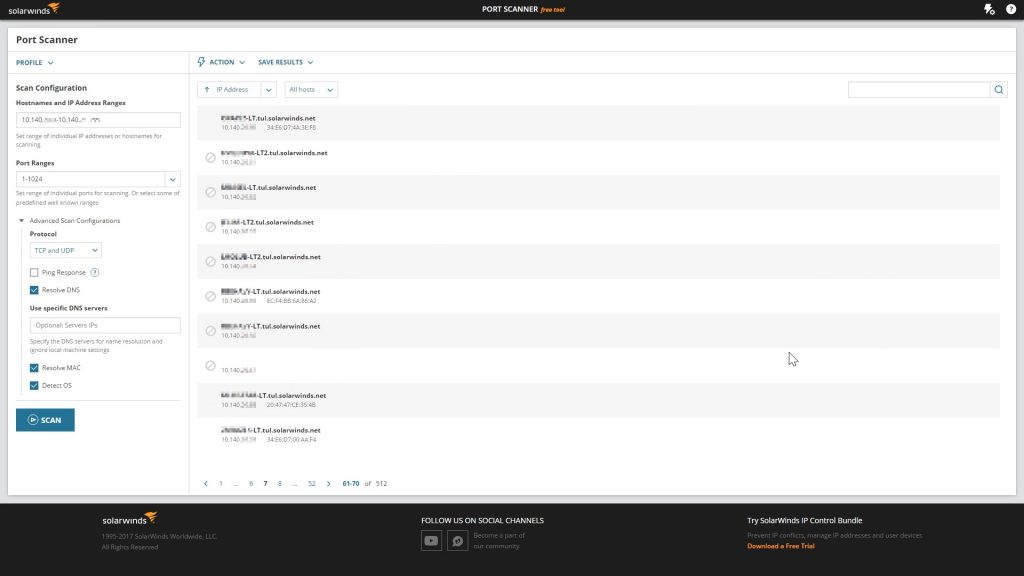
The installation process is very simple and clear. To download the tool, visit the Solarwinds website and click Download Free Tool. You will be asked to provide basic information and then you can download the tool. Follow the instructions after you have downloaded the tool to your system.
Unpack the zip file anywhere. Go to the extracted directory and run portscanner.exe.
Accept the license terms and click Accept.
- The tool now checks if all the requirements are installed on the system. If you miss something, it will be installed automatically.
- In this case, the “Prepare Application for First Use” dialog box offers to do it.
- Wait until the installation is complete and that is all. After that the tool is ready for use.
Analyze your network
Once the tool is set up and running, you will need to configure the scanning settings to detect your network. To do this, follow the instructions below:
- To scan your network, specify a range of IP addresses, hostnames or individual IP addresses. Use a semicolon (;) to separate individual IP addresses.
- Enter the range of ports to be determined.
- In the Advanced Scan Configurations section, you can select the type of protocol, for example. B. TCP or UDP.
- You can also specify specific DNS servers. If you want to recognize the operating system, activate the corresponding option.
- You can also save your scan configurations. This will create a profile for your current scanning configurations. To create a profile, click “Profile” and then click “Save as”.
- When you are finished, click Analyze.
- The tool launches the scan process and lists the detected devices in the right area.
Expert Tip: This repair tool scans the repositories and replaces corrupt or missing files if none of these methods have worked. It works well in most cases where the problem is due to system corruption. This tool will also optimize your system to maximize performance. It can be downloaded by Clicking Here
