Updated February 2025: Stop getting error messages and slow down your system with our optimization tool. Get it now at this link
- Download and install the repair tool here.
- Let it scan your computer.
- The tool will then repair your computer.
Trend Micro, the cyber security company, announced that it has found malware called BlackSquid that infects web servers with eight different vulnerabilities and installs mining software. The results were published in a blog on June 3.

In the report, malware targets web servers, network drives and removable media using eight different exploits and brute force attacks. More specifically, the software in question uses “EternalBlue; DoublePulsar; exploits for CVE-2014-6287, CVE-2017-12615 and CVE-2017-8464; and three ThinkPHP exploits for several versions”.
While the sample acquired by Trend Micro installs mining software based on the XMRig monero central processing unit (XMR), BlackSquid could also provide other payloads in the future. According to Trend Micro data, most of the malware cases in question were discovered in Thailand and the United States.
It also has a “worm-shaped” behaviour for transverse propagation, the researchers say. In other words, after a computer has been infected on a network, malware attempts to infect other systems on the network to spread the infection.
The overall objective is to compromise web servers, network drives and removable media to install XMRig, a Monero crypto currency miner script, on target machines.
How does BlackSquid infect a system?
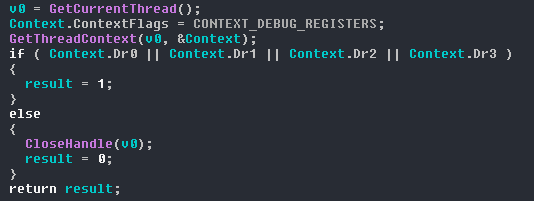
BlackSquid attacks systems via infected web pages, compromised web servers, removable media or network drives (for example, infected USB drives).
If not detected, the malware will install a version of the XMRig encryption script, but the attack does not stop there because the malware also searches for a graphics card on the infected system.
February 2025 Update:
You can now prevent PC problems by using this tool, such as protecting you against file loss and malware. Additionally, it is a great way to optimize your computer for maximum performance. The program fixes common errors that might occur on Windows systems with ease - no need for hours of troubleshooting when you have the perfect solution at your fingertips:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
Video card graphics processors can be large encryption crypto currency minors. When BlackSquid finds a GPU, it uses a second XMRig component to use hardware resources. In short, malware tries to exploit everything it can in a system to maximize encryption currency for attackers.
The malware stops the infection routine if at least one of the following conditions is met:
- The victim’s user name is included in a list of common sandbox user names:
- The training model is equal to a model included in a specific list;
- The device driver, process and/or dynamic link library is a specific list used by malicious code.
Remove BlackSquid Malware Exploits
Using the Task Manager
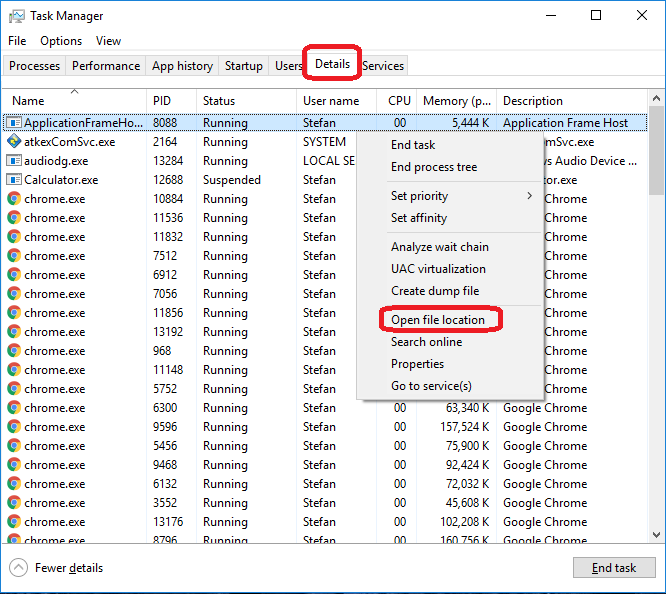
Press Ctrl + Shift + Esc to access the Task Manager. Go to the Process tab (details for Win 8/10). Carefully review the list of processes currently active on your PC.
If one of them looks suspicious, consumes too much RAM/CPU or has a strange description or no description at all, right-click on it, select Open File Location and delete everything in it.
Even if you do not delete the files, be sure to stop the process by right-clicking and selecting Stop Process.
Conclusion
BlackSquid is sophisticated malware, due to its evasion techniques and attacks, which can cause significant damage to the systems it infects. If successful, this malware can allow an attacker to increase unauthorized access and privileges, steal proprietary information, render hardware and software unusable, or launch attacks on an organization (or even from one organization to another).
But given the faulty code and deliberately ignored routines, we also believe that the cybercriminals behind this malware are likely to be in the development and testing phase; they may be exploring how they can get the most out of the attacks by having two components for mining, regardless of the GPU resources of the installed systems. In addition, they can try to set concrete objectives without raising a lot of capital. First, most of the exploits and techniques they chose were openly shared underground.
Expert Tip: This repair tool scans the repositories and replaces corrupt or missing files if none of these methods have worked. It works well in most cases where the problem is due to system corruption. This tool will also optimize your system to maximize performance. It can be downloaded by Clicking Here
