Updated February 2025: Stop getting error messages and slow down your system with our optimization tool. Get it now at this link
- Download and install the repair tool here.
- Let it scan your computer.
- The tool will then repair your computer.
In this article we will look at AWS security groups and how they can be used to protect your EC2 instances. We will also take a look at how to apply security patches to your instances and multitenancy options. Understanding AWS basics is essential if you want to provide services and resources in the AWS cloud. To learn the differences between computing services, see My AWS Compute Fundamentals course. This course is the first step toward learning AWS Basics and covers the basics of all AWS computing services and features to help you choose the most appropriate service for your project and your implementations.
AWS security groups and instance security
AWS Security Groups (SG) are assigned to EC2 instances and ensure secure access to protocols and ports. Each security group that functions as a firewall contains a set of rules that filter inbound and outbound traffic from an EC2 instance. Unlike the NACL (Network Access Control Lists), there are no deny rules. If there is no rule that explicitly allows a certain packet of data, it is rejected.
You should always try to restrict access using your security group to support access restriction at protocol and port level. Furthermore, you should implement a least privilege rule when developing and implementing rules in security groups. Allow only the necessary access and do not use over-authorized access as it can lead to future security breaches and security vulnerabilities.
Each security group should have a name so that it can be easily distinguished from others. A description is optional but allows to add additional context information to better understand the security groups. Security groups refer to VPC. Therefore, during security groups you must specify which VPC the SG is in. Make sure that you select the correct VPC for the resource you want to protect.
Differences between AWS security groups and traditional firewalls
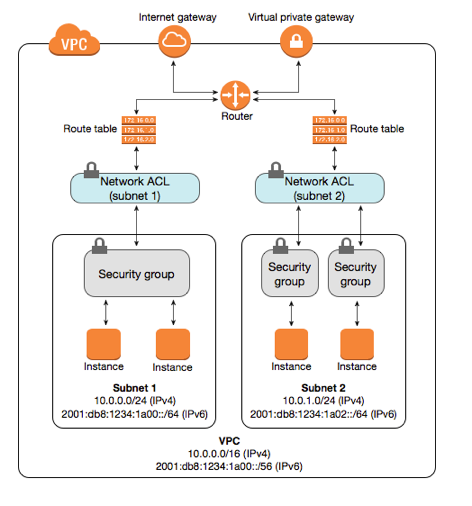
Traditional firewalls can be tough and restrictive. However, in AWS security groups, you can specify allowed rules. You cannot ban traffic.
This is very important because almost all traffic is blocked without any rules. If a data packet does not contain a certain allow rule, it will be rejected immediately.
February 2025 Update:
You can now prevent PC problems by using this tool, such as protecting you against file loss and malware. Additionally, it is a great way to optimize your computer for maximum performance. The program fixes common errors that might occur on Windows systems with ease - no need for hours of troubleshooting when you have the perfect solution at your fingertips:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
Use several AWS security groups
You can specify one or more security groups for each EC2 instance with a maximum of five for each network interface. In addition, each instance on your VPC subnet can be assigned a different set of security groups. For data traffic to reach an instance, Amazon EC2 evaluates all rules for all security groups assigned.
Once rules have been added or modified, they are automatically applied to all instances assigned to a security group.
With tools such as CloudGuard, you can visualize the cloud security situation at the infrastructure level (VPC, security groups, EC2 and RDS instances, Amazon S3 dumpster, elastic load balancers, etc.). E.) And interactively determine the configuration is drifting.
Create a security group
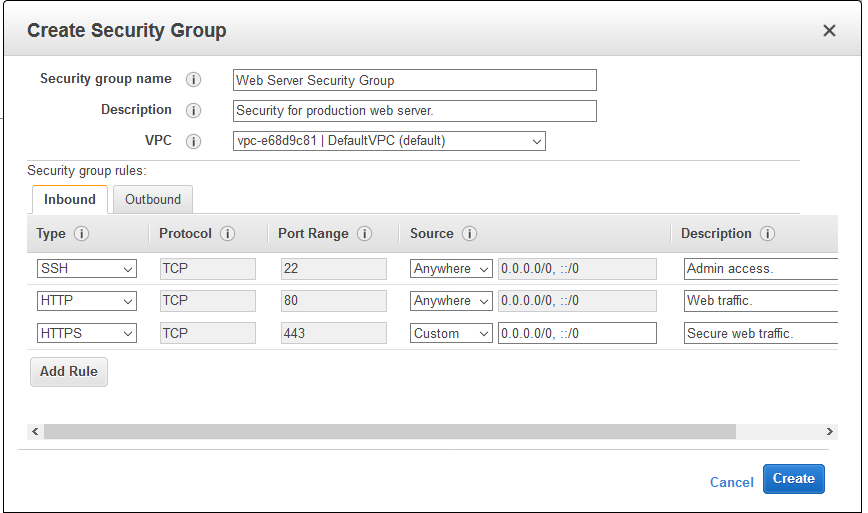
You can create a custom security group using any of the following methods. You must provide the VPC for which you are creating the security group.
- How to create a security group
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- Select the Security Groups in the navigation area.
- Select Create security group.
- In the “Basic information” section, do the following.
- Enter an informative name and a short description of the security group. The name and description can be up to 255 characters long and can consist of letters a-z, A-Z, 0-9, spaces and ._-: / () #, @ [] + = &; {}! $ * On.
- For a VPC select the VPC where you want to create the security group. A security group can only be used in the VPC where it was created.
- You can now add security group rules or add them anytime after the security group has been created. For more information about adding security group rules, see VPC. See the section Adding rules to a security group.
- Select “Create”.
View your security groups
You can view information about your security groups in any of the following ways.
- How to view your security groups
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- Select the Security Groups in the navigation area.
- A list of your security groups. To view detailed information about a particular security group, including rules for inbound and outbound traffic, select its identifier in the “Security group identifier” column.
Best practices for using AWS security groups
There are a number of best practices and tips that can be used to leverage AWS security groups and improve the overall security situation:
- You should enable flow log maintenance on your VPC. These logs give you a complete picture of the type of traffic that flows through the VPC. You can use flow logging to identify problem traffic and get valuable information. This can also help you to troubleshoot access and security issues. For example, you can use the Trace log to see if there are any legitimate security groups.
- EC2 security groups should not have large port ranges. In this case, security holes can be easily detected or used.
- Do not allow unlimited access to RDS instances. RDS registers failed connection attempts, but does not block recurring errors. Leaving an instance open to the Internet would create a risk of brute force attacks. You should also restrict access to clusters in Amazon Redshift.
- Less frequently use discrete security groups to avoid configuration errors that could compromise your account.
- Restrict access to outgoing ports only for certain ports or destinations. Also do not allow unlimited inbound access to unusual ports.
- For example, do not allow access via port 445, which is commonly used for Common Internet File System (CIFS). In addition, only allow FTP on port 20 or 21 and only after it is limited to the necessary objects.
There are a number of recommendations for AWS security groups depending on the technologies, services and protocols used (for example, MySQL, Oracle Database, Remote Desktop or SMTP). Also take the time to familiarize yourself with them before using security groups.
Expert Tip: This repair tool scans the repositories and replaces corrupt or missing files if none of these methods have worked. It works well in most cases where the problem is due to system corruption. This tool will also optimize your system to maximize performance. It can be downloaded by Clicking Here
