Recently, there have been many reports of users being infected with the “ROTE” virus on their computer, slowing its use and preventing access to certain files. In this article, we inform you about what the virus is, its severity, and we also inform you about methods to get rid of it permanently.
Rote Ransomware is a crypto virus that allows access to the victim’s files. Cyber scammers request a ransom in exchange for the decryption software or the infected files remain encrypted.
What is the Rote Ransomware Virus?
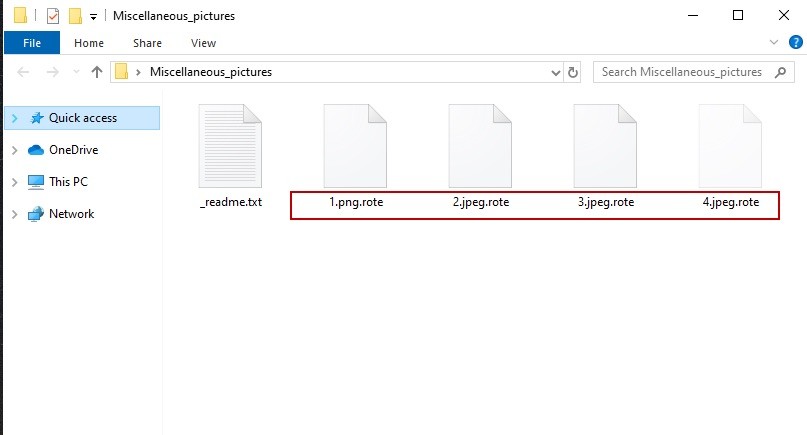
Rote Ransomware is a virus that encrypts personal and valuable files stored on the target computer. This malware is another variant of the popular ransom software STOP/DJVU. If valuable documents, pictures, videos and other data become unusable and are renamed by adding a .rote extension, this means that the red virus is infecting your computer.
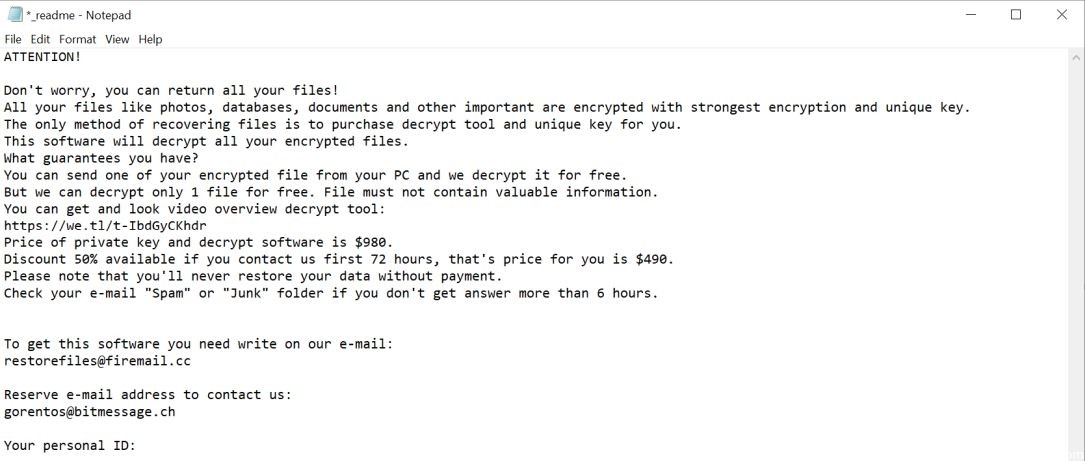
The next thing you will notice is the location of the a_readme.txt file on your Windows desktop. This is the ransom note that contains information about what happened to your files. The Rote Virus explains that your files were encrypted with the strongest encryption and the most unique key. The cyber-scammer points out that there is no other way to recover your files than to pay the ransom.
To benefit from this decryption software, you must pay the required amount. If you contact the author of malicious software within 72 hours, the ransom price is $490. But if you contact them after 72 hours, you have to pay 980 dollars. He says that once you give the money, they will return the decryption software.
We must remind you that paying the ransom is not a solution to this problem. When the Rote virus hits your computer, the only way to recover all encrypted files is to back up your data. To avoid further damage to your system, you must remove this virus from your computer. Immediate removal is essential to prevent illegal and harmful activity inside the machine.
How did the Rote Ransomware get on my computer?
Rote Ransomware is spread through spam emails with infected attachments or by exploiting vulnerabilities in the operating system and installed programs.
Cybercriminals send spam from an email with false header information, so you think it comes from a shipping company like DHL or FedEx. The email tells you that they tried to deliver a package to you, but failed for some reason. Sometimes emails claim to be notifications of a shipment you have made. However, you can’t resist the curiosity of knowing what the email refers to – and opening the attachment (or clicking a link in the email). And with that, your computer is infected with the Red Ransom software.
This ransom software has also been observed in victim attacks by hacking into open Remote Desktop Services (RDP) ports. Attackers look for systems with RDP and then try to force the password for the systems.
February 2025 Update:
You can now prevent PC problems by using this tool, such as protecting you against file loss and malware. Additionally, it is a great way to optimize your computer for maximum performance. The program fixes common errors that might occur on Windows systems with ease - no need for hours of troubleshooting when you have the perfect solution at your fingertips:
- Step 1 : Download PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista – Microsoft Gold Certified).
- Step 2 : Click “Start Scan” to find Windows registry issues that could be causing PC problems.
- Step 3 : Click “Repair All” to fix all issues.
To remove the Rote virus from your computer
- Restart in safe mode
- Press CTRL + SHIFT + ESC simultaneously and go to the Process tab. Try to find out which processes are dangerous.
- Right-click each of them and select Open File Location. Then scan the files with our free online antivirus software:
- After you have opened your folder, complete the infected processes and then delete their folders.
Note: If you are sure that something is part of the infection, remove it even if the scanner does not mark it. No antivirus program can detect all infections.
- Hold down the Start key and R – copy and paste the following items and click OK :
- notepad %windir%/system32/Drivers/etc/hosts
- A new file is opened. If you are hacked, there will be a number of other IP addresses associated with you below. Take a look at the image below:
- Type msconfig in the search field and press Enter. A window will open:
- Go to Start -> Disable inputs with “Unknown” manufacturer.
- Please note that Ransomware may even include a false supplier name in the process. Be sure to check all the processes here that are legitimate.
- Type Regedit in the Windows search box and press Enter. Once inside, press CTRL and F simultaneously and enter the name of the virus.
- Look for the ransom in your records and delete the entries. Be extremely careful – you may damage your system if you delete entries that are not linked to Ransomware.
Enter one of the following in the Windows search box:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete all in Temp. The rest is just looking at everything that has been added recently. Don’t forget to leave us a comment if you have any problems!
Retrieve encrypted files with Rote Virus Ransomware.
Method 1: Use Shadow Explorer.
If you have enabled file history on your Windows machine, you can use Shadow Explorer to recover your files. Unfortunately, some Ransomware viruses can remove these hidden copies with an administrative command to prevent you from doing so.
Method 2: If you try to decrypt your files using third-party decryption tools.
There are many antivirus providers who have decrypted several ransomware viruses in recent years and published decryption software for them. There is a good chance that your ransom virus uses the same encryption code as a decryptable virus, you can recover the files. However, this is not a guarantee, so you should try this method with copies of the original encrypted files, because if a third-party program changes its encrypted structure, it can cause permanent damage. Most of the ransom virus decryptors currently available can be seen during the visit of the NoMoreRansom project – a project that is the result of joint efforts by researchers around the world to develop decryption software for all software ransom viruses. Just go by clicking on the following LINK and find your decryptor for the Ransomware version and try it out, but don’t forget to make a backup first.
Method 3: Use data recovery tools.
This method is proposed by several experts in this field. It can be used to scan the sectors of your hard disk and re-encrypt encrypted files as if they had been deleted. Most ransomware viruses usually delete a file and make an encrypted copy to prevent such file recovery programs, but not all are as sophisticated. You may therefore be able to recover some of your files with this method.
